RESOURCE ARTICLE
CMS Security Best Practices 2026: Protect Your Website from Vulnerabilities

Seven out of ten hacked websites run on outdated CMS versions; don’t let yours be one of them.
A CMS makes it simple to create and manage a website, but it also introduces risks. Attackers know that millions of businesses rely on platforms like WordPress, Drupal, Joomla, and Shopify, and they constantly scan for weak points. According to security researchers, more than 70% of hacked websites in recent years were running outdated versions of their CMS. That means most of those breaches could have been prevented with simple updates and maintenance.
The damage from a CMS attack goes far beyond the technical. A hacked site can result in stolen customer information, reputational harm, financial losses, and even regulatory fines. Restoring trust after an incident is far more difficult than preventing one in the first place. That is why having a set of clear best practices is essential.
Control Access with Role-Based Permissions
One of the most overlooked aspects of CMS security is access management. Many organizations leave their default accounts untouched or give too many users administrative rights. Every unnecessary privilege increases your risk.
To tighten control:
- Create specific roles for contributors, editors, and administrators.
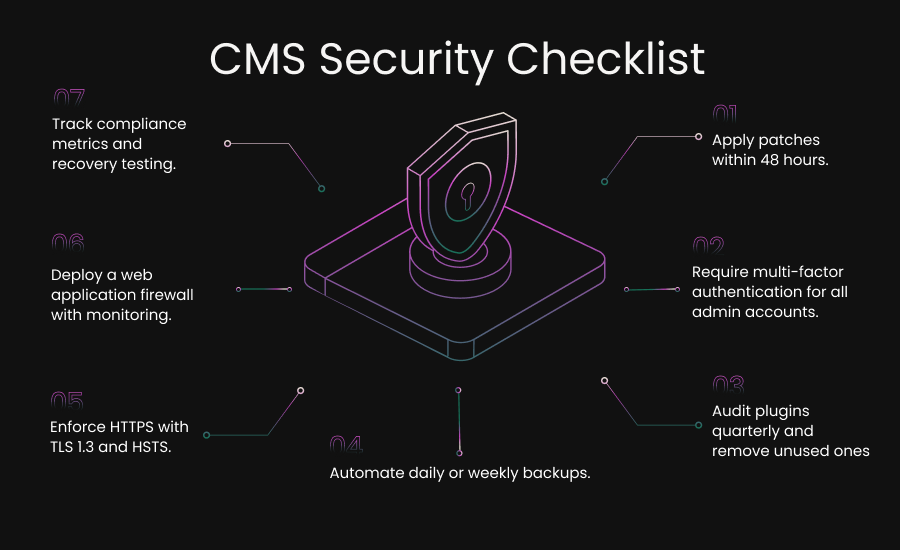
- Enforce strong password policies and require multi-factor authentication for all accounts with elevated privileges.
- Regularly audit user accounts and remove inactive profiles or old team members.
- Apply session timeouts so accounts automatically log out after periods of inactivity.
For example, a freelance content writer does not need access to plugin installation or server configuration. Limiting what each person can do ensures that even if their account is compromised, the attacker cannot take full control of the system.
Be Careful with Plugins and Extensions
Plugins and extensions are double-edged swords. They add valuable functionality but are also a favourite target for hackers. Outdated or poorly coded plugins often become backdoors into websites.
Best practices for plugin security:
- Always install plugins from official repositories or trusted developers.
- Look for a history of frequent updates and an active support community.
- Remove plugins that are no longer used, since inactive plugins can still be exploited.
- Replace plugins that have been abandoned by their developers.
- Test new plugins in a staging environment before deploying them on the live site.
Consider keeping a plugin inventory where you track each plugin, its developer, update frequency, and date of last patch. This makes audits much easier and ensures you never forget a vulnerable add-on lurking in your system.
Stay Current with Updates and Patches
Attackers often exploit known vulnerabilities that already have fixes available. In fact, most breaches do not involve new or sophisticated exploits, but old issues that were never patched.
To keep your CMS safe:
- Enable automatic updates for core CMS software whenever possible.
- Apply security patches within 48 hours of release.
- Update themes and plugins alongside the CMS itself.
- Maintain a simple dashboard or spreadsheet to track patch status across systems.
- If you manage multiple sites, consider using a centralised patch management tool.
A useful metric here is the Patch Compliance Rate, which shows the percentage of systems updated within a defined timeframe. High compliance means you are staying ahead of attackers who rely on old vulnerabilities.
Use HTTPS and Strong Encryption
Visitors expect to see the padlock symbol in their browser, and search engines give ranking preference to secure sites. More importantly, encryption prevents attackers from intercepting data while it travels between a user’s browser and your server.
Here is what to do:
- Install an SSL certificate and configure your site to enforce HTTPS.
Use TLS 1.3 for stronger protection against known vulnerabilities.
- Turn on HTTP Strict Transport Security (HSTS) so browsers never attempt insecure connections.
- Monitor certificates to ensure they are renewed before expiration.
Even if your site does not handle payments, SSL is critical. Login details, contact forms, and customer messages all involve sensitive data. Without encryption, this information can be intercepted and misused.
Deploy a Web Application Firewall and Monitoring
A firewall acts as a filter between your CMS and the internet. It blocks malicious traffic and can stop many attacks before they reach your system. Modern WAFs can detect patterns of suspicious activity, such as SQL injection attempts or brute force login attacks.
Alongside a firewall, you should have monitoring in place. This includes:
- Automated alerts for unusual behaviors.
- Reports on login attempts and failed logins.
- Notifications about unexpected changes to files or configurations.
- Analytics dashboards that help track suspicious spikes in traffic.
.png)
Two metrics are worth tracking: Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). The shorter these times are, the more resilient your CMS will be against threats.
Backups and Disaster Recovery
Even with strong security controls, no system is perfect. That is why backups and recovery planning are essential. Losing your site content, customer records, or order history without a backup can cripple a business.
Practical steps include:
- Automating daily backups for high-traffic or dynamic websites.
- Storing copies on separate servers or cloud storage.
- Encrypting backups to keep them secure.
- Testing the restoration process to ensure backups actually work.
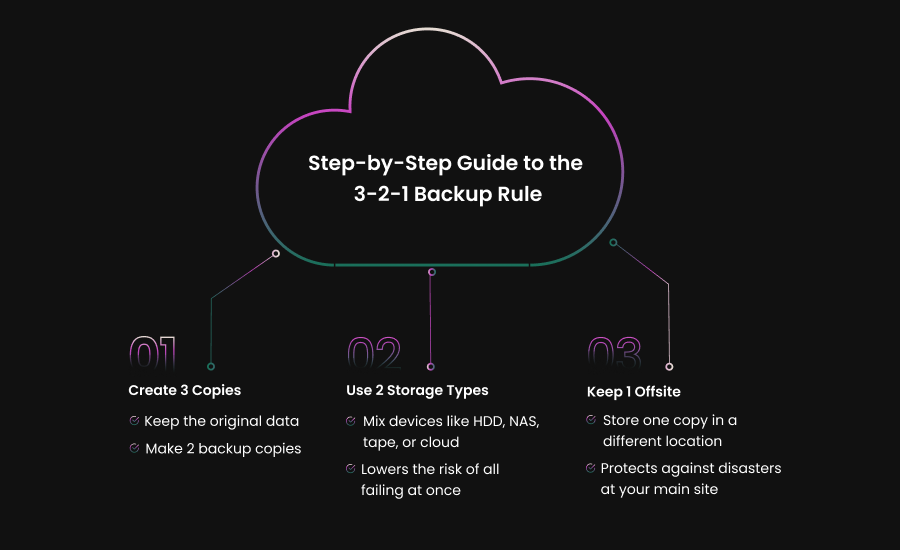
Follow the 3-2-1 rule: keep three copies of your data, in two different formats, with one copy stored offsite. This simple strategy protects you against ransomware, accidental deletion, and hardware failures.
Meet Compliance Standards and Track Security KPIs
If you handle personal data, you may already be subject to regulations such as GDPR or industry standards like SOC 2. Even if compliance is not legally required, adopting these frameworks demonstrates responsibility and builds trust.
Some useful security KPIs include:
- Number of failed logins attempts per week.
- Percentage of systems patched within 30 days.
- Average time taken to apply updates after release.
- Backup success rates and recovery testing results.
Tracking and reviewing these measures helps you spot weak areas before they become critical problems.
Understand Common CMS Attacks
Attackers rely on tried and tested methods that target common weaknesses. By learning about them, you can put safeguards in place.
Each of these attacks has caused major breaches across industries. The good news is that most can be prevented with basic measures applied consistently.
Wrapping It Up!
Keeping a CMS secure requires discipline and consistency. There is no single fix that protects you from every threat, but applying these practices together creates a strong defense. Start with access control and plugin audits, keep your system patched, enforce encryption, and add monitoring for early detection.
Combine those efforts with regular backups and compliance tracking, and you give your website a level of resilience that most attackers will not bother to challenge. The result is a safer environment for your data, your customers, and your business as a whole.
When discipline and consistency matter most, Uzera helps you put every best practice into action. From access control to monitoring, backups, and compliance, Uzera keeps your CMS resilient so you can focus on growth instead of threats.
Frequently Asked Questions
How often should I back up my CMS?
You should back up your CMS daily if your site handles high traffic or online transactions. For smaller, less active sites, weekly backups are usually enough.
What is the most common CMS attack?
The most common CMS attack is still SQL injection, which can cause serious damage. Brute force login attempts are also widespread and need strong defenses.
Do I really need SSL on all sites?
Yes, you do need SSL on all sites. It’s required by browsers, improves search rankings, and builds user trust. Even small blogs should run on HTTPS.
How can I keep plugins safe?
To keep plugins safe, install only those from trusted developers, review their update history, and remove any plugins you no longer use.
What is the 3-2-1 backup rule?
The 3-2-1 backup rule means keeping three copies of your data, storing them on two different types of media, and making sure one copy is offsite.







.svg)


.svg)

